Today we are excited to announce Graylog Illuminate v1.4.
This release includes the addition of Office 365 content, which provides deeper visibility into Azure Active Directory and Exchange Online logs along with new alerts for a more granular level of notifications.
NEW: OFFICE 365 CONTENT
The new Office 365 content focuses on Microsoft Azure AD and Exchange Online. This is especially useful when you are running hybrid deployments.
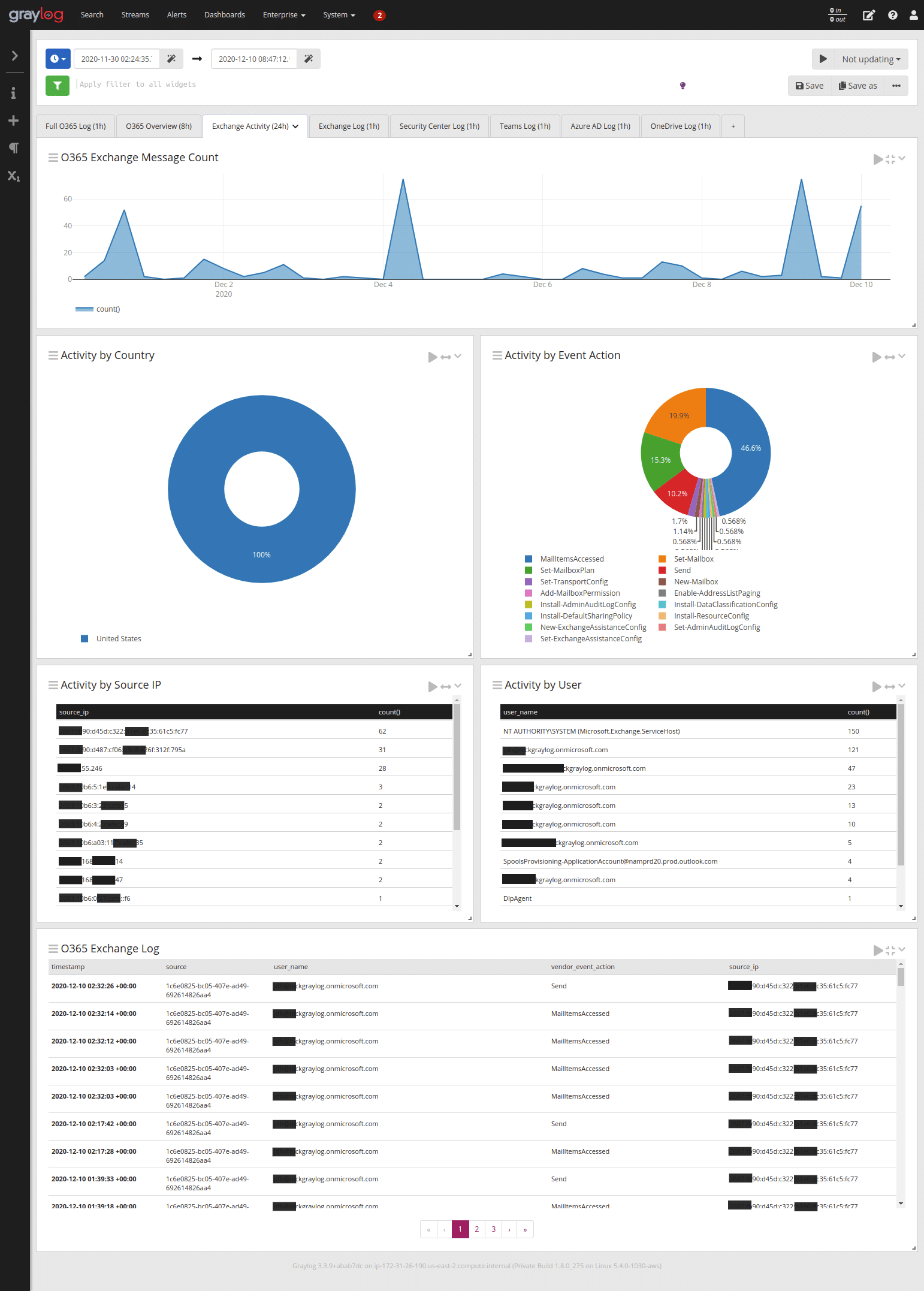
This new content gives you deeper visibility into Azure AD logs.
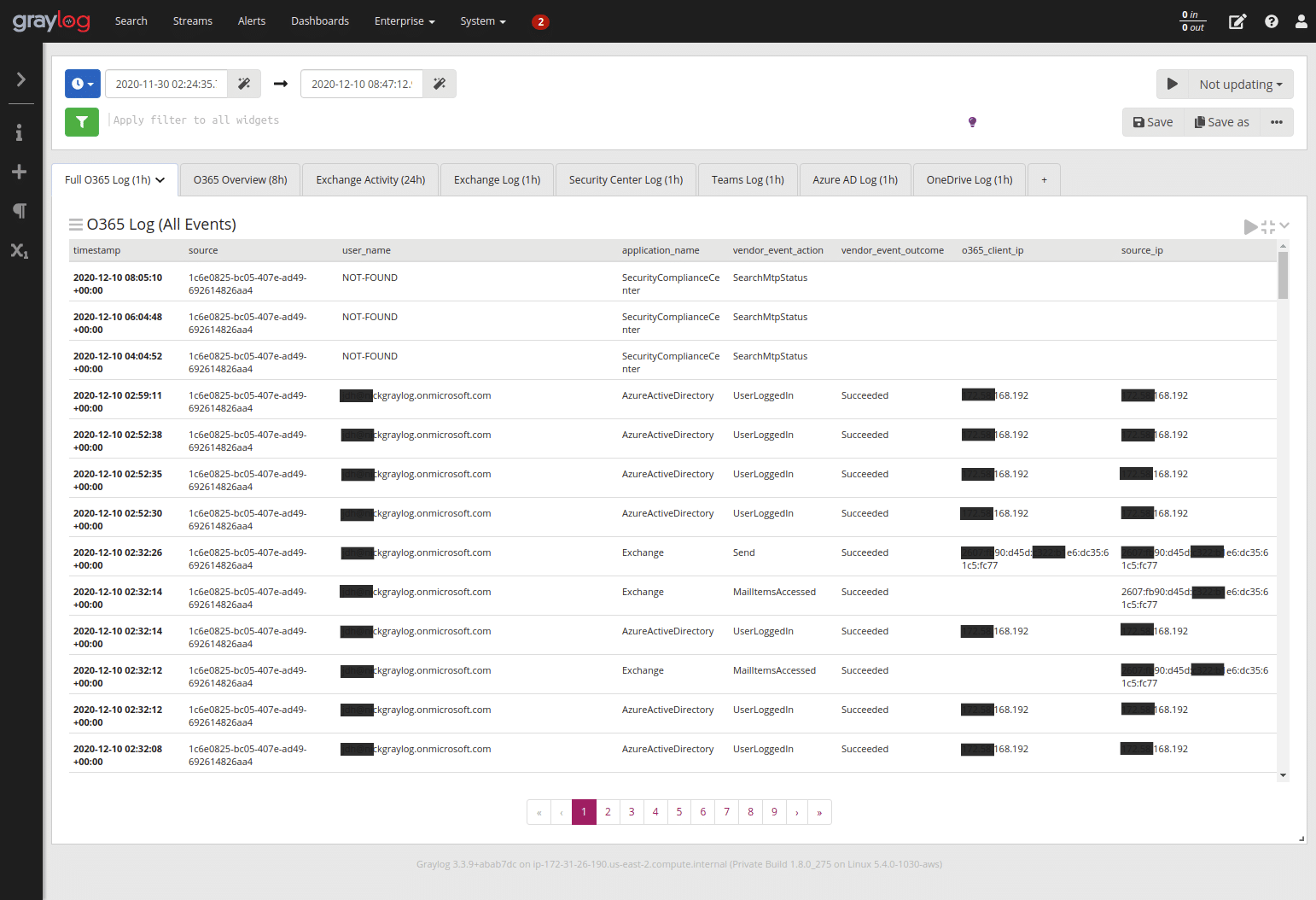
Focusing specifically on email senders, attachments, viruses, as well as normal account lockouts presented in Illuminate authentication dashboard for enriched local data such as firewalls and endpoints (i.e., anything not in Microsoft cloud.)

ADDED: WINDOWS AND GENERAL ALERTS
Illuminate Core comes with three new alerts:
Windows
- Security event log clearance
- Failed logon failed due to accessing unauthorized host
General
- Logins from different countries in a time window
IMPORTANT NOTE
For those using Illuminate for Windows devices, this will be the last release of Illuminate that contains “copy” normalization rules. Any existing Windows content that relies on the copy functionality will not function with future versions of Illuminate. Please contact Graylog Technical Support if you have any questions about the deprecation of the “copy” normalization content and/or functionality.
BUG FIXES
- Windows Spotlight: Fixed issue with improper categorization of Windows Kerberos events (#92,#92)
- Windows Spotlight: Rename metric in Account Drill Down / Summary / Network Bytes Over Time (24h) #75
- Events Spotlight: Provided replacement alert “Illuminate:Events:3;Windows:Multiple accounts Locked Out” (previous version had incorrect field)
- Core: IP Processing pipeline now identifies IPv4 loopback addresses (#88)
- Windows Normalization for NXLog: Nxlog 2.1 should instead be nxlog 2.10 #84
- Rename Illuminate objects to drop “Graylog” #80
- Palo Alto URL filtering dashboards aggregate based on previous URL category field #93



