In cybersecurity, old tactics rarely die — they just get repackaged. Attackers continue to revive long-standing techniques, dressing them up with minor tweaks to stay effective. Living Off the Land Binaries (LOLBins) are a prime example: legitimate Windows tools repurposed for malicious ends. Despite being around for decades, these methods still work — often because many organizations aren’t equipped to spot or stop them. Mustang Panda’s recent use of MAVInject shows exactly why defenders need to stay sharp.
The LOLBin star for today’s blog is Microsoft Application Virtualization Injector (MAVInject) which is (un)surprisingly still kicking since its first buzz around 2017. We’ll cover its particular role in a novel attack chain reported by Trend Micro researchers whereby the threat group Mustang Panda combines legitimate components with malicious payloads to reduce likelihood of detection.
In this blog we’ll emulate the infection chain described in the report and analyze the activity it produces in Graylog. Throughout and at the end of the post, we share threat hunting and detection approaches that you can apply in your own environments.
Attack Overview
The attack likely starts with a spear-phishing email attachment. When executed by the victim, IRSetup.exe is used to drop multiple files to the system. In the case of the Trend Micro report, the files were placed in a newly created C:\ProgramData\session directory.
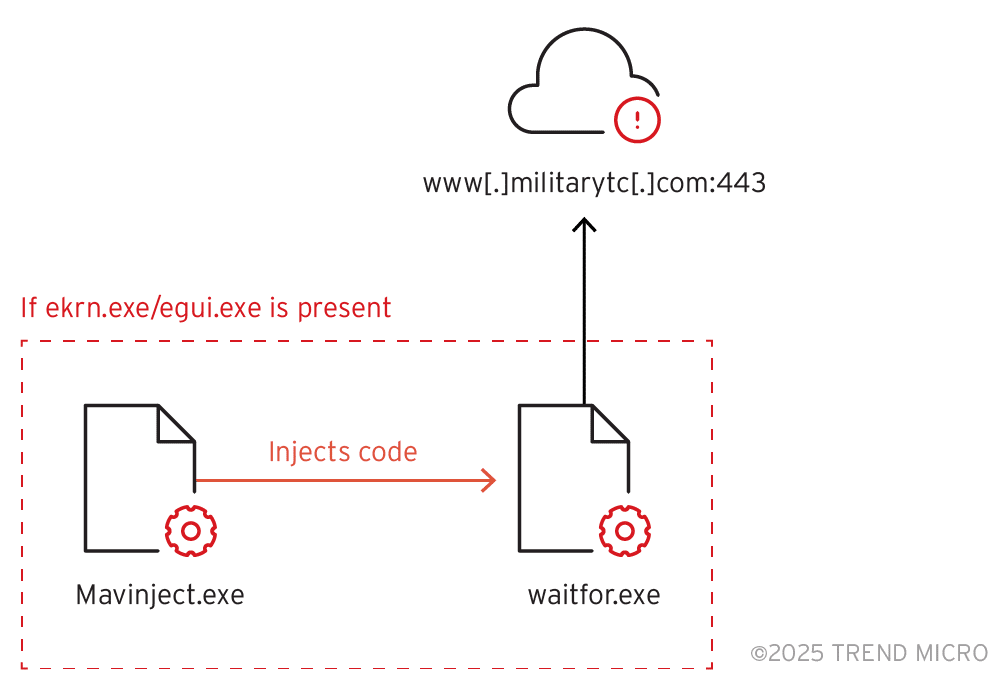
The report’s execution flow diagram seen below shows how the kill chain progresses from the initial dropper all the way to payload execution, ultimately leading to Command and Control (C2) communication to the attacker-controlled server www[.]militarytc[.]com over port 443.
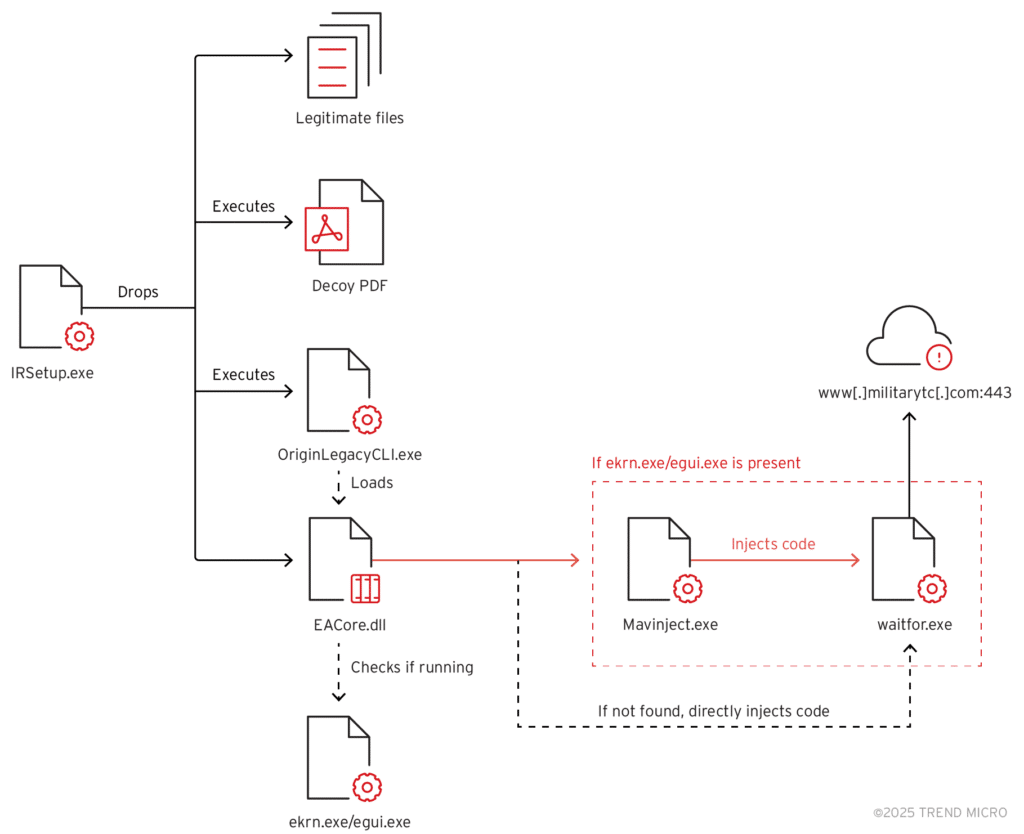
Key elements
- IRSetup.exe opens a decoy PDF to distract the victim while the malicious payload is deployed in the background.
- The legitimate Electronic Arts (EA) application OriginLegacyCLI.exe is executed to sideload EACore.dll, which contains the actual malicious functionality. The DLL is a modified version of Mustang Panda’s TONESHELL backdoor.
- The malware checks if ESET security software is running on the host by looking for its associated processes ekrn.exe or egui.exe.
- If present, it uses MAVInject to inject itself into the legitimate Windows application waitfor.exe and triggers code that establishes the connection to its C2 server.
- Otherwise, MAVInject is skipped and the code is directly injected into waitfor.
“DLL? Sideloading?? Injection???”, one might be thinking as they read through that. Not to worry, these concepts will be demystified as we emulate the chain ourselves later.
It seems that Mustang Panda might’ve found this use of MAVInject to fly under the radar of ESET software specifically, though that remains unclear – ESET since responded that this technique is not a bypass to its protections.
Persistence
While researching this attack, we came across a report on Any.Run that exhibits a similar kill chain. It includes a persistence mechanism via registry Run key that wasn’t mentioned in the original report.
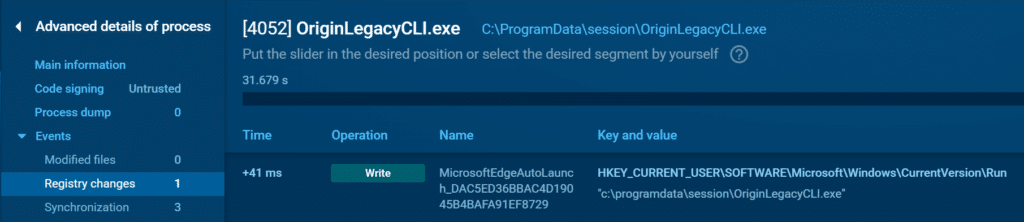
This mechanism enables the malware to maintain its foothold on the compromised host. Even if the system is restarted, it will be re-infected once the user logs in.
Emulating the Adversary
Lab setup
To emulate and analyze the attack, we’ve set up a lab environment with Graylog Enterprise 6.1.7 and Illuminate Windows Security Event Logs Content Pack enabled to parse, normalize and enrich the logs. Graylog Security is also included to integrate Sigma rule detections.
A Windows Server 2022 system will serve as our “victim host”. Its configuration sends System, Security, PowerShell/Operational, and Defender event logs via Graylog Sidecar to our Graylog instance. Auditing is explicitly enabled for process execution (command line included), registry changes in commonly abused locations, and file system changes in the ProgramData folder.
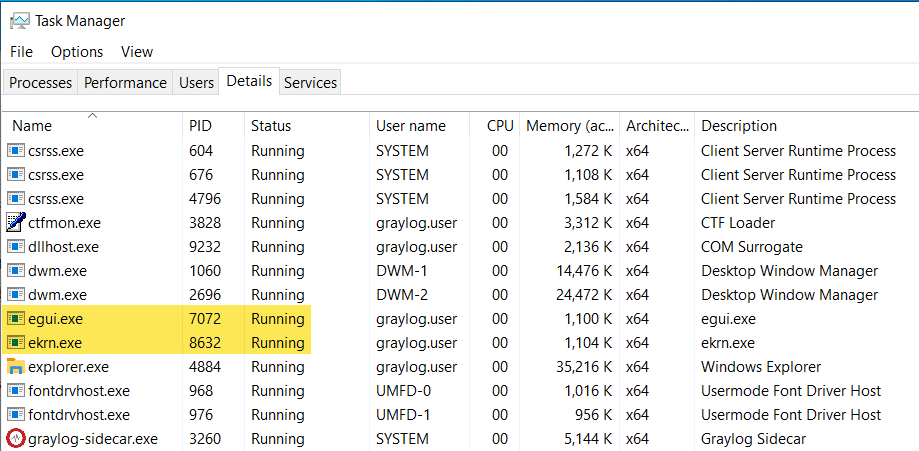
We’ve built custom binaries — programs, that is — that closely mimic the malware’s core functionality based on Trend Micro’s analysis, all bundled into a custom IRSetup dropper. To trigger the Mavinject flow, we placed “dummy” programs that mimic ESET running processes. This works because the malware only checks for the process names.
Detonating the mimic malware
Aaaaand, detonate💥!
We see that the mimic dropper wrote files to the ProgramData\session folder and auto-launched the decoy PDF. Waitfor.exe is also running in Task Manager.
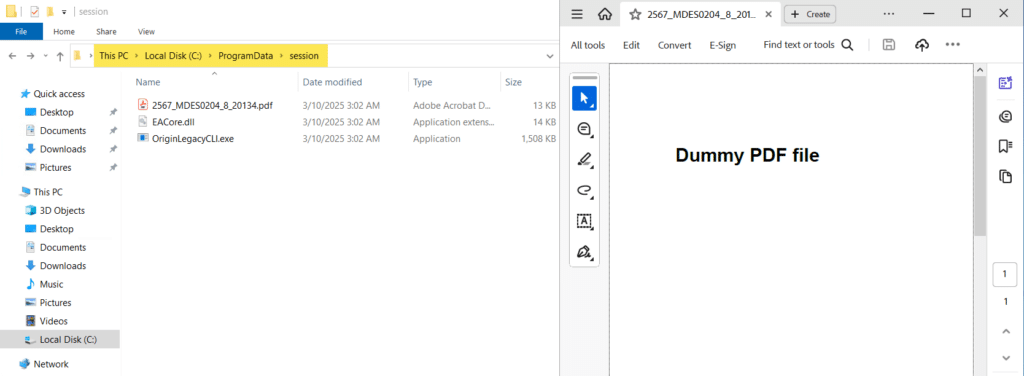
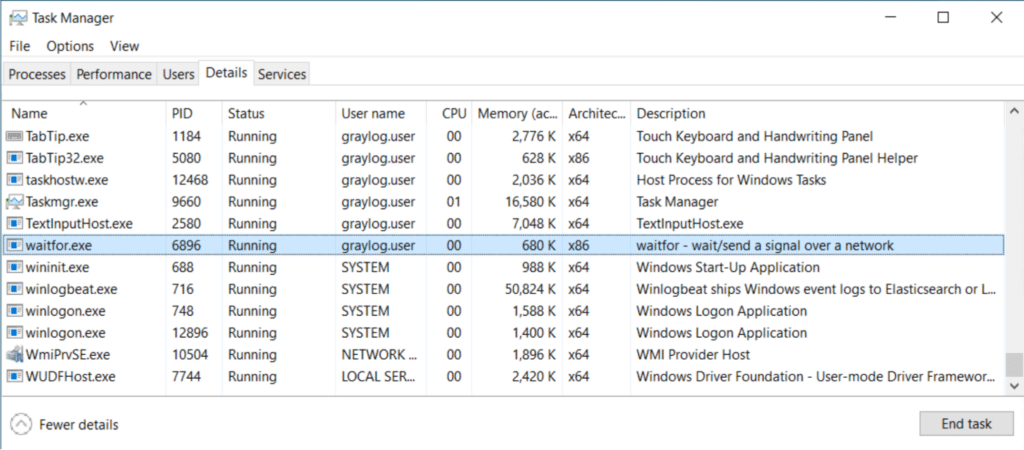
It looks like the infection chain of our mimic malware followed through. Let’s hop over to Graylog to get a detailed view of the activity that occurred.
IRSetup dropper
IRSetup.exe itself isn’t malware — it’s created using a legitimate Windows software installer builder named Setup Factory, in this case abused to drop and execute the malicious files. Attackers favor legitimate tools to blend into environments and make it harder for detection logic to separate malicious from benign activity. It also saves them the trouble of implementing these components themselves.
While we don’t have the actual Setup Factory installer, our mimic dropper does replicate its main function. In the screenshot below we see activity marking the beginning of the infection, sorted by ascending time (read top to bottom):
- Event ID 4688 (process creation) shows IRSetup.exe being executed
- This is followed by file system events where the installer writes the PDF, EACore.dll, and OriginLegacyCLI.exe files to C:\ProgramData\session
- The installer proceeds to execute OriginLegacyCLI.exe
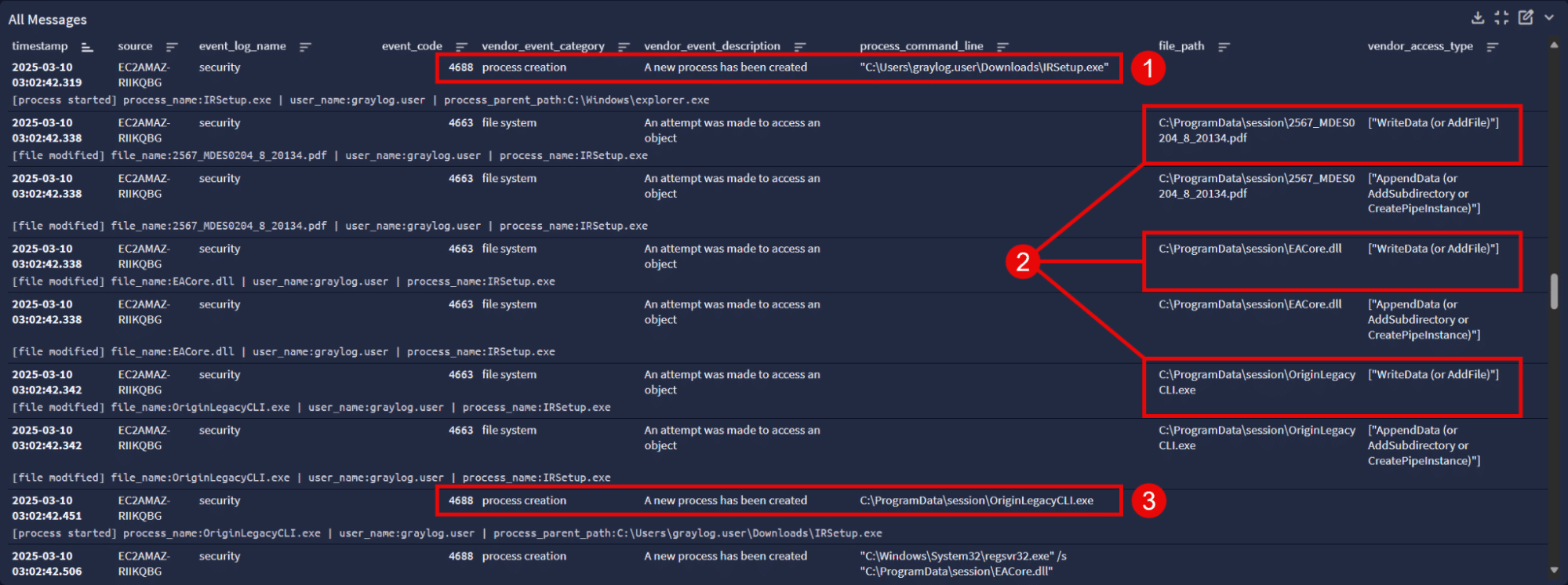
This is where the fun begins (props if you know that reference). Shown below is the rest of the infection chain following OriginLegacyCLI.exe execution. We’ll break down each part and write some threat hunting queries along the way.
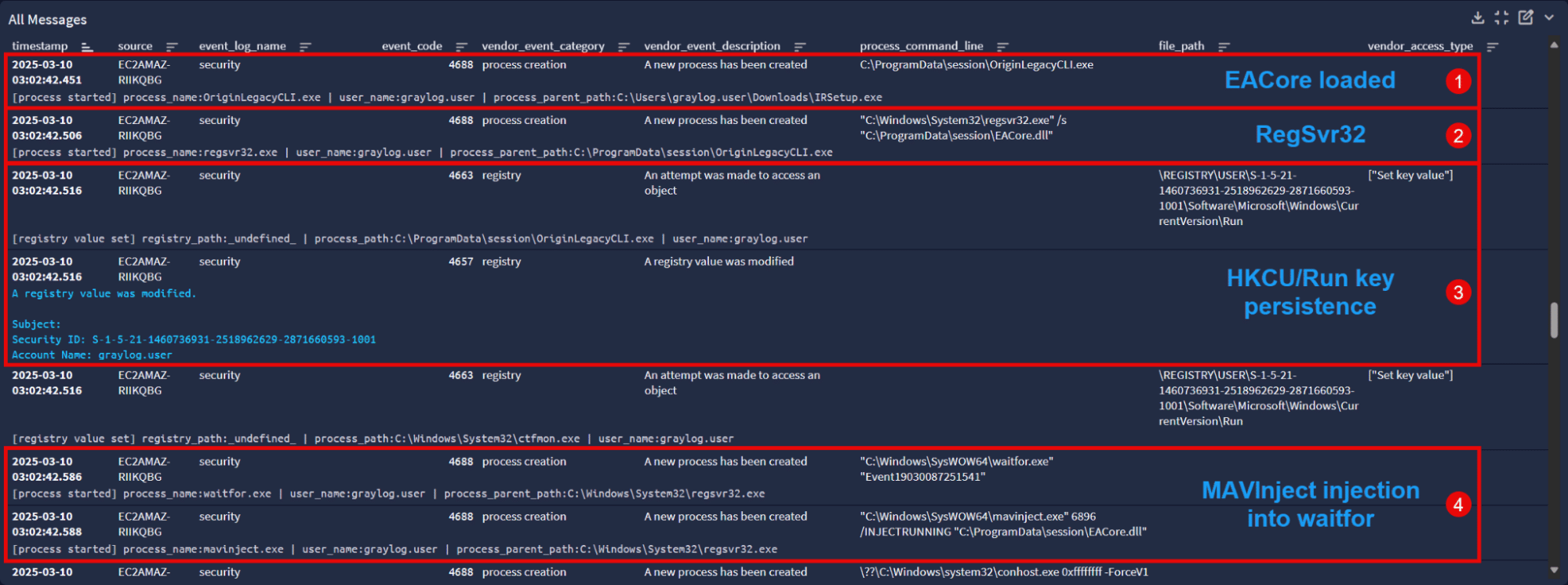
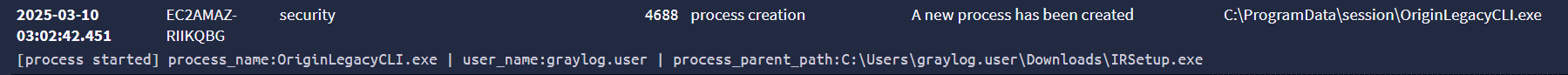
EACore DLL sideloading
OriginLegacyCLI.exe gets executed in block 1. We don’t have the visibility from these Windows events to see EACore.dll getting sideloaded as a result (Sysmon would help with that), but we can infer that it happened based on the activity following.
So, what is DLL sideloading? Before that even, what’s a DLL?
A DLL, or Dynamic Link Library, is a shared file used by Windows programs to perform certain functions without having to include all the necessary code within the program itself. Developers load and import ready-made code libraries from DLLs into their applications so they don’t have to reinvent functionality that’s already been written.
DLL sideloading is a technique where a legitimate application unknowingly loads a malicious DLL instead of the intended one, allowing attackers to execute their code while appearing legitimate. It’s similar to DLL hijacking, the difference being that the attacker places the trojanized DLL alongside the target application EXE and directly invokes the application to proxy execute the DLL.
In the Mustang Panda infection chain, the attacker positions the legitimate, signed 3rd-party application OriginLegacyCLI.exe and a tampered EACore.dll in the same directory. When OriginLegacyCLI.exe runs, it follows a search order to look for the DLL it needs by name, in this case “EACore.dll”, and load it.
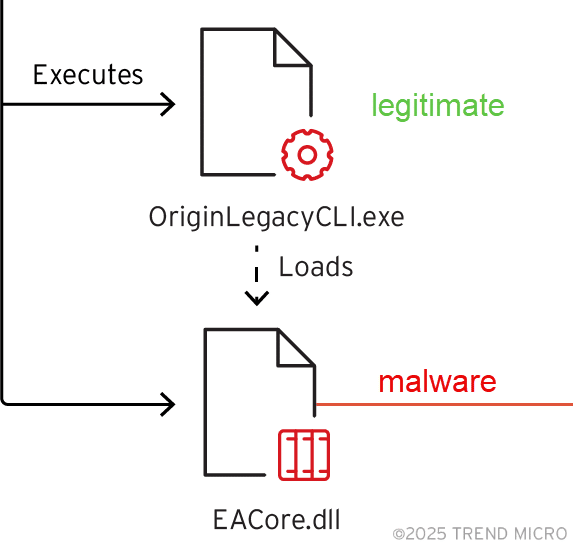
DLLs in the same folder as the application take priority in the search order hierarchy. OriginLegacyCLI finds that the backdoored EACore.dll matches its search first, and loads it unaware that it’s been swapped. Upon load or import of functionality, the malicious code housed in the DLL gets executed.
This method is highly effective because it exploits trust in legitimate applications and is difficult to identify, helping malware evade security detections. For this reason it’s often a preferred execution method by Red Teams and threat actors alike.
ESET check and RegSvr32
At this point the malicious code in EACore is running under the mask of OriginLegacyCLI, and we move to block 2.
According to the Trend Micro report, the malware checks for ESET running on the system and, if present, “registers EACore.dll using regsvr32.exe to execute the DLLRegisterServer function”, seen in the command line:
“C:\Windows\System32\regsvr32.exe” /s “C:\ProgramData\session\EACore.dll”
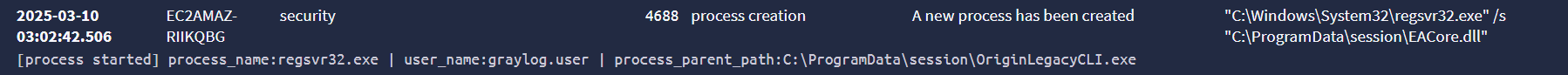
Put simply, RegSvr32 is a Windows utility that can be abused to proxy execute malicious code. Instead of EACore invoking its own function, it takes the long way of having RegSvr32 do it. The result is the start of the next infection phase now under the parent process of regsvr32.exe.
Again, we see the use of a built-in Windows utility in an attempt to thwart detections.
DLL injection via MAVInject
Now for what we’ve all been waiting for. If you’re here, you’ve probably weathered the technical hailstorm that was the last few sections, and to that I give a swift salute.
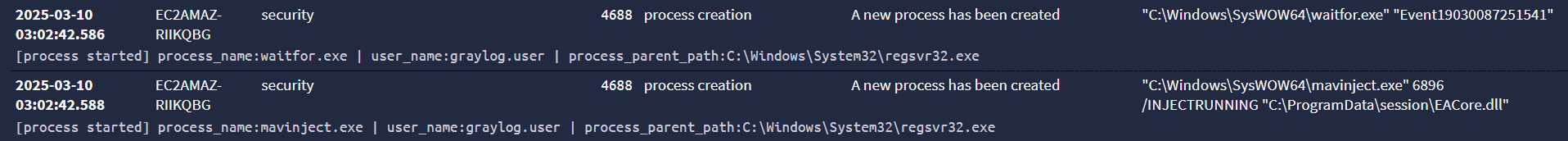
We’re now in block 4, where we see waitfor.exe process creation followed by DLL injection into that process using MAVInject.
So, DLL injection.

In this context, DLL injection is a method of executing malicious code inside of another, often legitimate, running process. It takes a DLL and forces the separate process to load and execute it, enabling malicious activity under the guise of that process.
As we see above, the malware first launches the legitimate Windows program waitfor.exe with the intent to inject into it.
“C:\Windows\SysWOW64\waitfor.exe” “Event19030087251541”
It captures the process ID (PID) 6896 of the newly spawned waitfor.exe to be referenced during injection.
It then runs Mavinject.exe to inject itself, EACore.dll, into waitfor.exe referencing its PID 6896.
“C:\Windows\SysWOW64\mavinject.exe” 6896 /INJECTRUNNING “C:\ProgramData\session\EACore.dll”
Once EACore.dll is injected into waitfor.exe, it establishes a network connection to the C2 server for control over the compromised system.
That’s the gist. If you’re here for the details, it triggers an execution flow to decrypt, allocate and execute shellcode that opens a reverse shell to the C2 and sends information about the victim host. The C2 server communicates with the host using a custom command protocol.
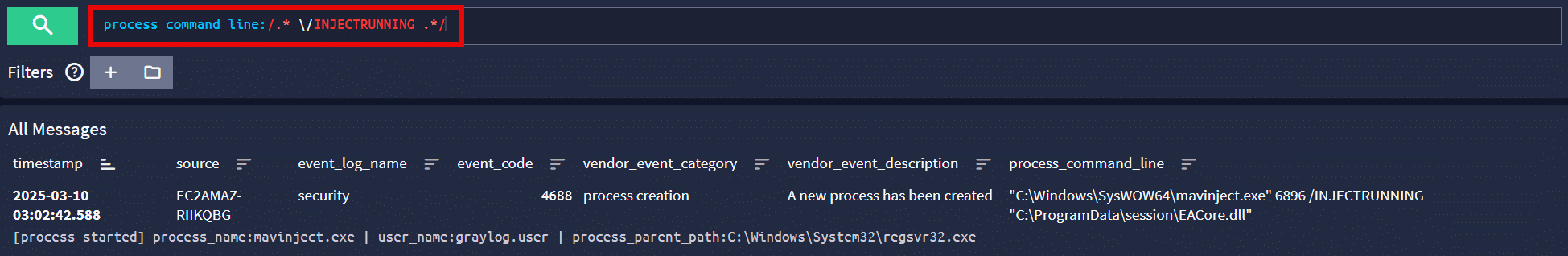
We can hunt for MAVInject DLL injection using the following query in Graylog.
process_command_line:/.* \/INJECTRUNNING .*/
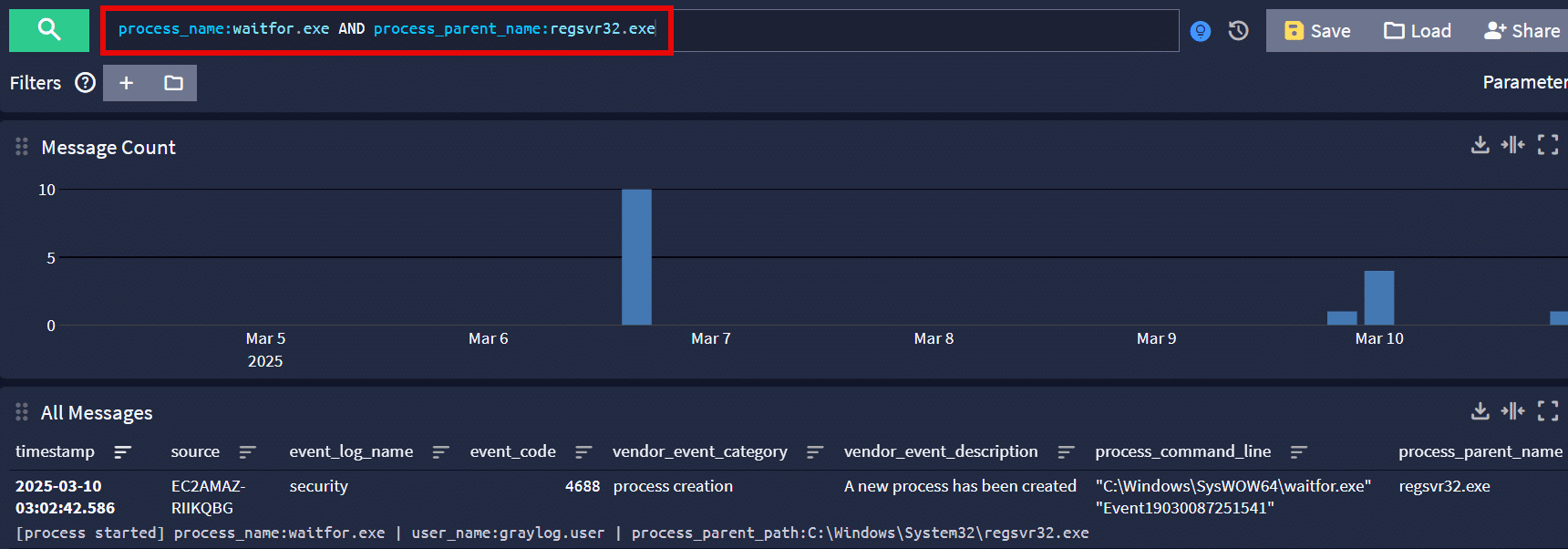
Looking for waitfor.exe spawned under regsvr32.exe is another useful query.
process_name:waitfor.exe AND process_parent_name:regsvr32.exe
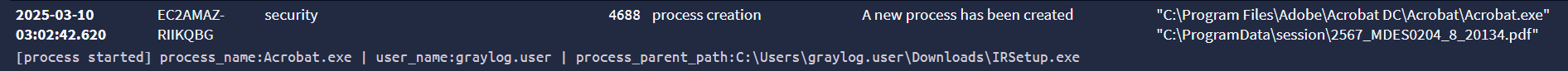
Decoy PDF
As a little bonus, our mimic dropper also opens the decoy PDF.
Run key persistence
Going back to the start of this blog post, we identified that the malware might also set autostart persistence in the registry to survive reboots.
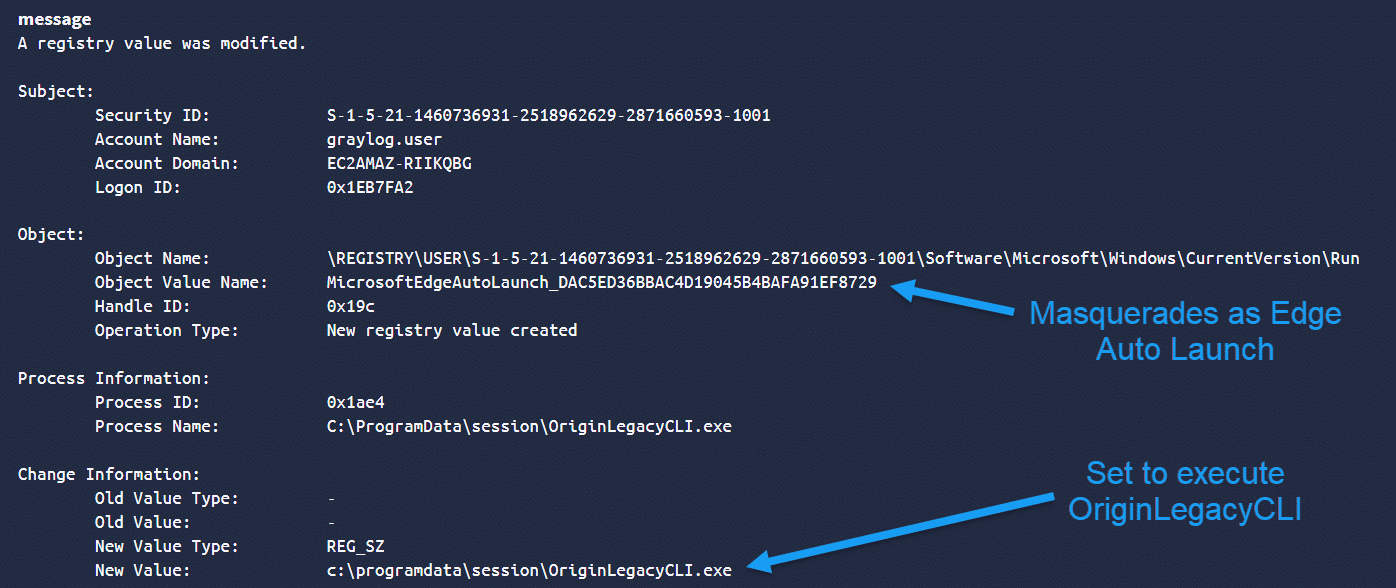
In block 3 above, there are registry modification events that show the malware creating a Run key under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Viewing the details of Event ID 4657 (registry value was modified) in Graylog, we see that the key name masquerades as Microsoft Edge Auto Launch. It’s set to execute OriginLegacyCLI.exe (and therefore the EACore.dll TONESHELL backdoor) upon user logon in order to re-infect the system.
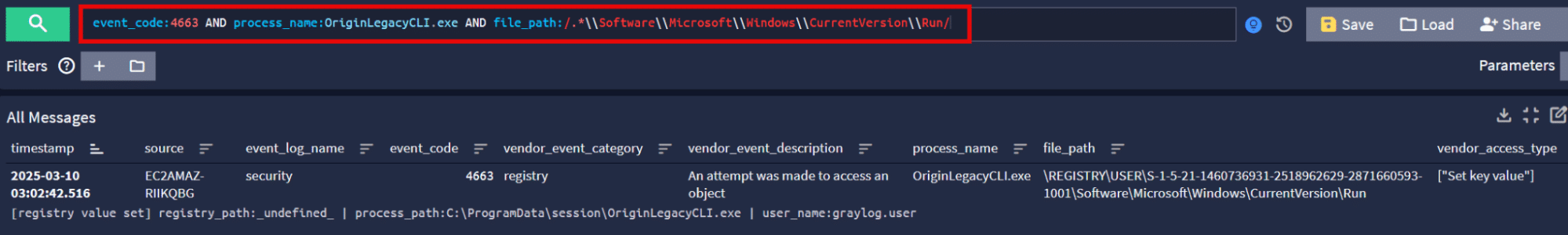
We can hunt for registry HKCU\Run key persistence with event IDs 4657 or 4663. Here is an example query using ID 4663 to uncover registry Run key writes from OriginLegacyCLI.exe (Bear in mind that this won’t catch instances where OriginLegacyCLI is renamed or replaced, remove the process_name condition to cover those).
event_code:4663 AND process_name:OriginLegacyCLI.exe AND file_path:/.*\\Software\\Microsoft\\Windows\\CurrentVersion\\Run/
Detections
We recommend the following SigmaHQ rules to detect this attack chain and similar events:
- Mavinject Inject DLL Into Running Process
- Potentially Suspicious Child Process Of Regsvr32 (waitfor.exe added)
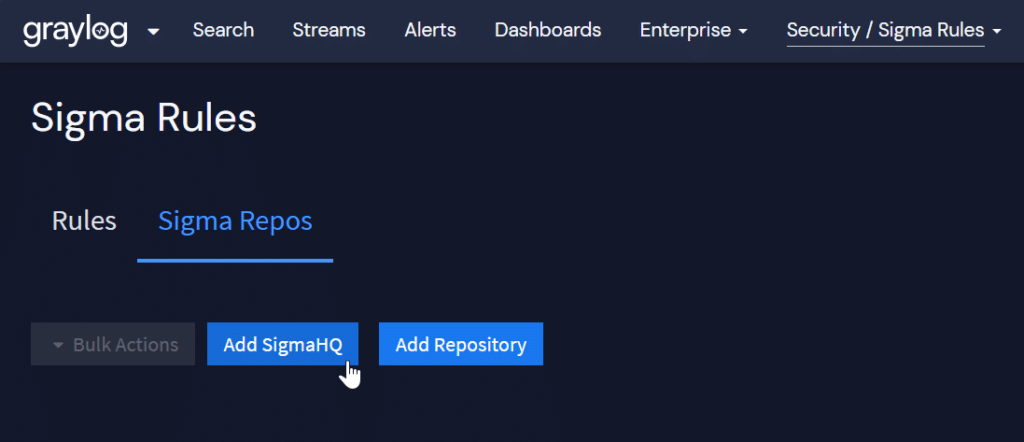
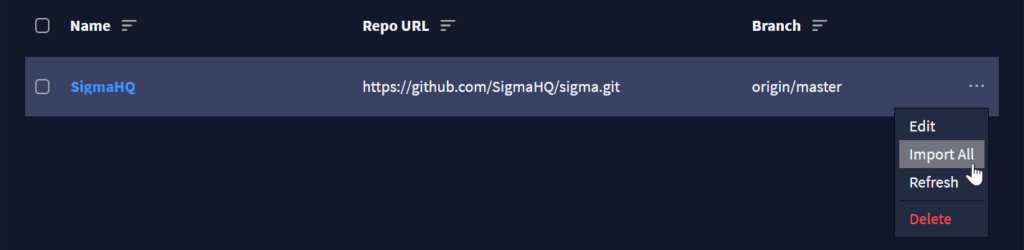
We can easily add these rules with Graylog Security. Add the SigmaHQ repository and import all, then search for and enable the rules.


For “Potentially Suspicious Child Process of Regsvr32” you will have to add waitfor.exe to the Image list, like so.
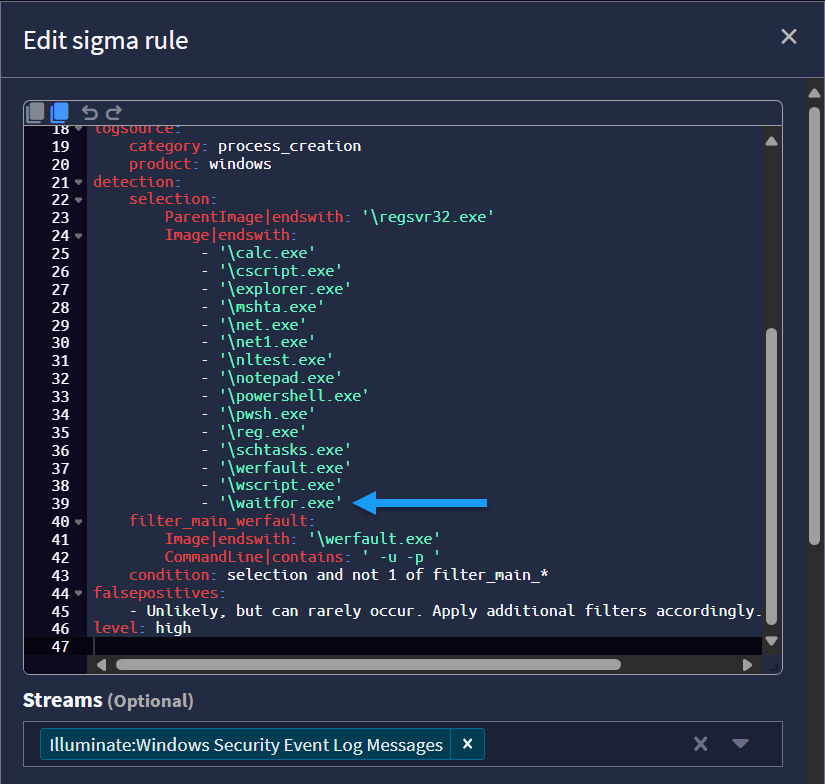
Indicators
These indicators will primarily be useful for hunting past intrusions that went unnoticed. They have little effectiveness in detecting future intrusions by Mustang Panda as threat actors tend to burn or alter their tools and infrastructure between campaigns.
OriginLegacyCLI.exe (legitimate application targeted for sideloading) SHA-256:
91357E6E5A8DB3D9D3B23CE4368425A148683287D917D927EE2BB6E835C87EBE
EACore.dll (modified TONESHELL backdoor) SHA-256:
DC673D59A6A9DF3D02E83FD03AF80E117BEA20954602AE416540870B1B3D13C4
Registry HKCU/Run key (persistence mechanism) Name:
MicrosoftEdgeAutoLaunch_DAC5ED36BBAC4D19045B4BAFA91EF8729
Value:
“c:\programdata\session\OriginLegacyCLI.exe”
www[.]militarytc[.]com:443 (C2 server hostname and port)
193[.]56[.]255[.]179 (C2 server IP address)
In general, look for Mavinject.exe execution and outbound network connections from unexpected Windows programs. Ensure that execution of Potentially Unwanted Programs (PUPs) and unauthorized software is tracked in your environment.
Graylog Detections
Graylog has provided the Sigma Rules and Indicators here to share threat detection intelligence with those not running Graylog Security. Note that Graylog Security customers receive a content feed including Sigma Rules, Anomaly Detectors, Dashboards, and other content to meet various security use cases.
To learn how Graylog can help you improve your security posture, contact us today or watch a demo.



