Graylog Illuminate for Networks automates the visualization, management, and correlation log data. It centralizes all generated log data into a single location. The data is aggregated and correlated for visibility so you can monitor and analyze the data, identify any malicious activity occurring within your network, isolate the source of the activity, and quickly respond to the threats. This creates more effective security monitoring and enables comprehensive auditing.
CENTRALIZED NETWORK DATA BRINGS FASTER RESPONSE TIMES
Built by Graylog’s Enterprise Intelligence team, Illuminate for Networks eliminates the manual set up necessary to detect, monitor, and analyze network issues across your IT infrastructure.
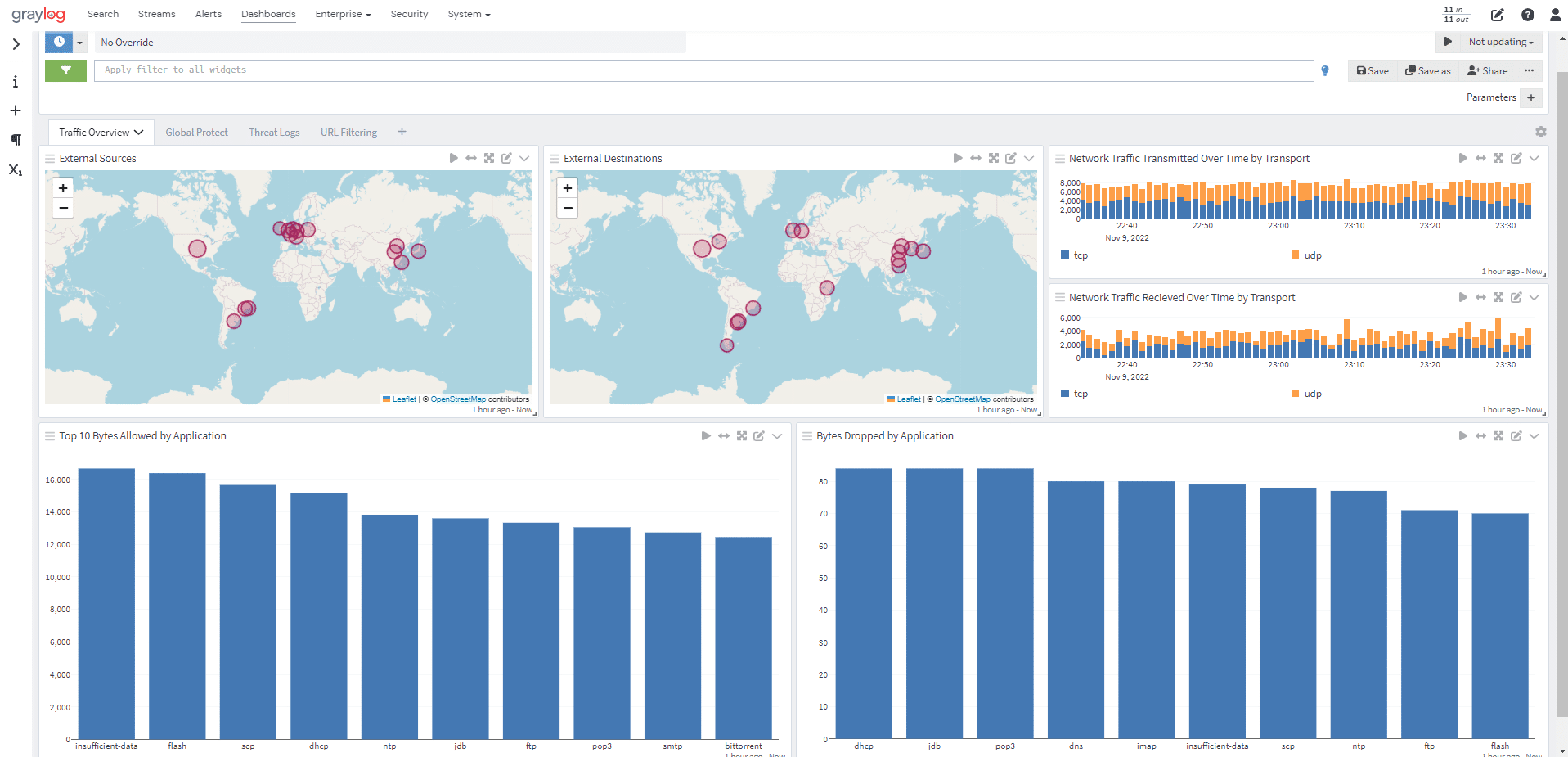
Initially, Illuminate for Networks will spotlight activities detected by Palo Alto. Graylog offers a more robust set of dashboards where you can aggregate and correlate network traffic from different devices into one central location.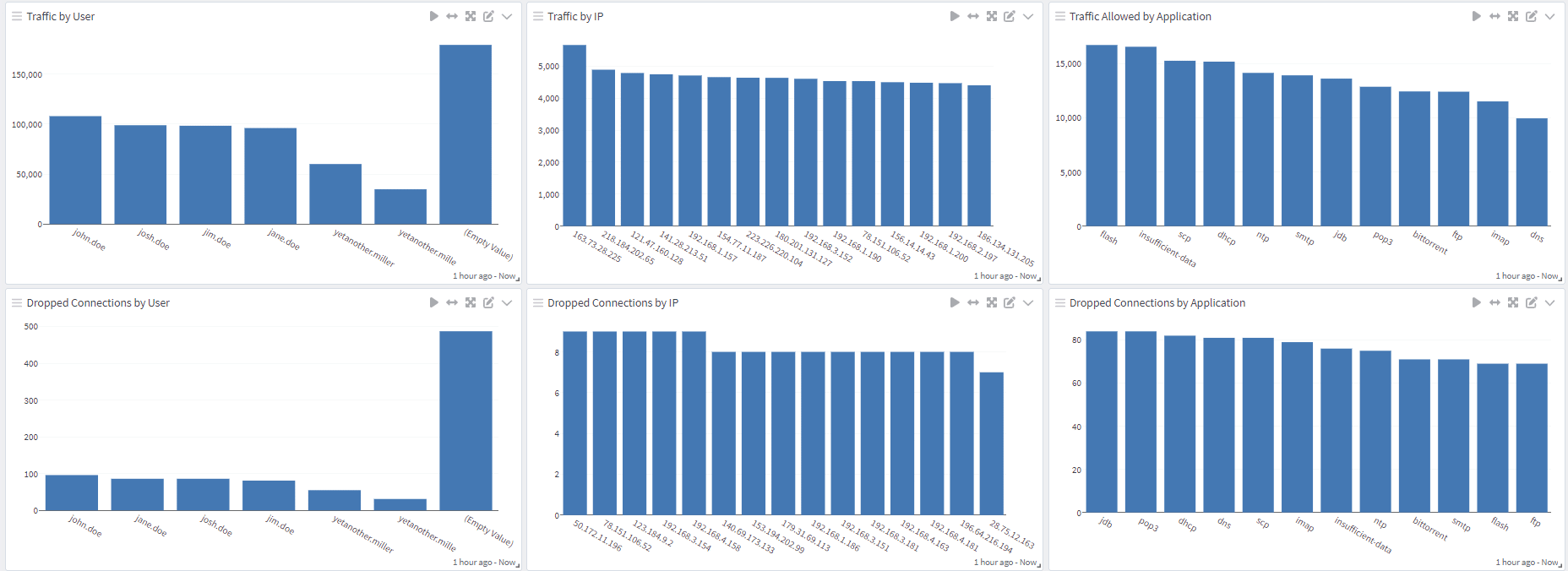
Illuminate for Networks layers logic on the Enterprise input plugin for Palo Alto 9 in order to pull all of your network data into Graylog. This enables you to see all of your Palo Alto data aggregated and correlated into one chart for faster analysis and threat hunting. With data fields aligned, properly classified, and useful information added to the log messages, you can also build “universal” dashboards for deeper account and device investigation.
ROBUST MONITORING ANALYSIS WITH GRAYLOG DASHBOARDS
The Graylog Illuminate dashboards offer a more robust experience for monitoring and analyzing your network traffic. The pre-built content dashboards provide the means for your team to visualize what the network activities that Palo Alto is seeing on the network and identify any anomalies you want to investigate further.

If you’re troubleshooting a problem or investigating a potential security threat, Graylog eliminates the need to work in different interfaces by aggregating and correlating the data into one dashboard. This streamlines your daily tasks by separating the important data from all the noise. Front and center you can immediately see things like the number of alerts that have triggered during a specified time frame, user activity, maybe traffic via VPNs to foreign countries you might be interacting with, basically the type of data your team wants to see with one search.

