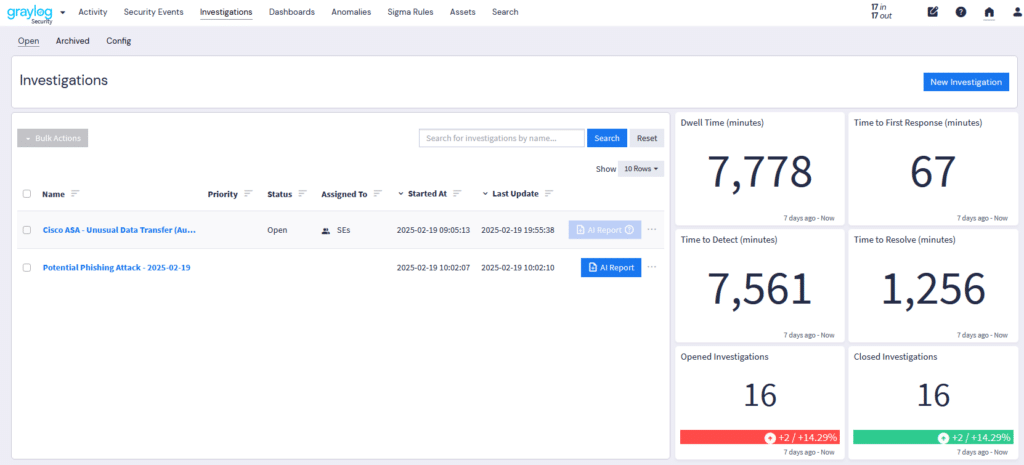
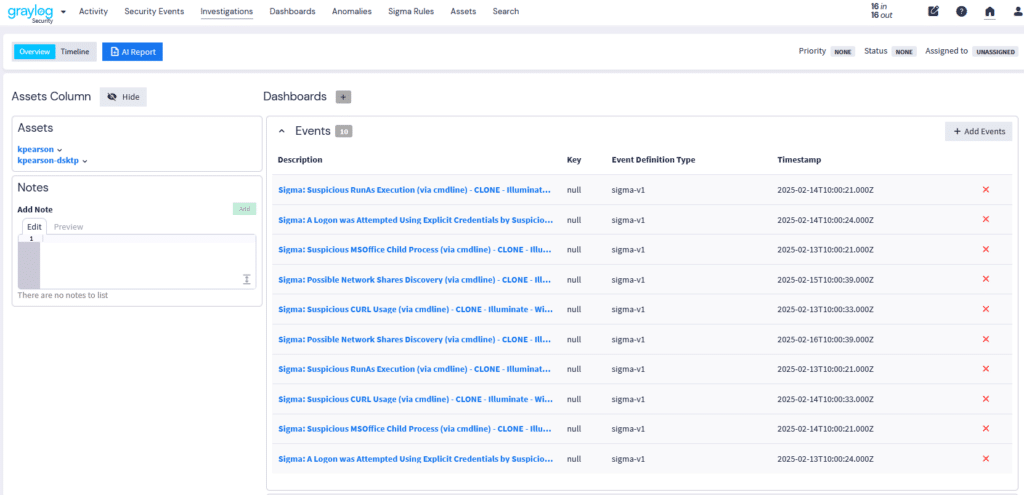
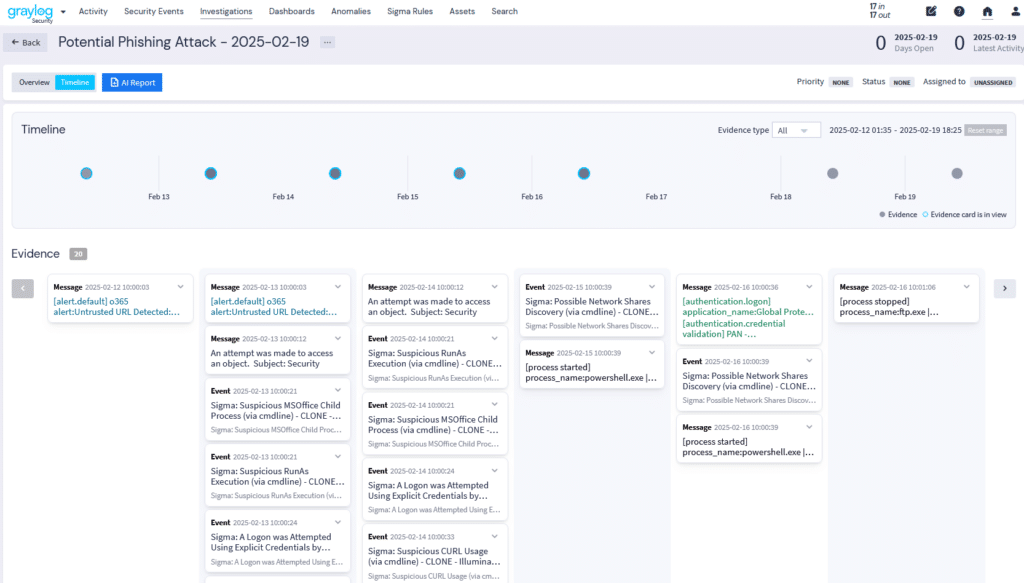
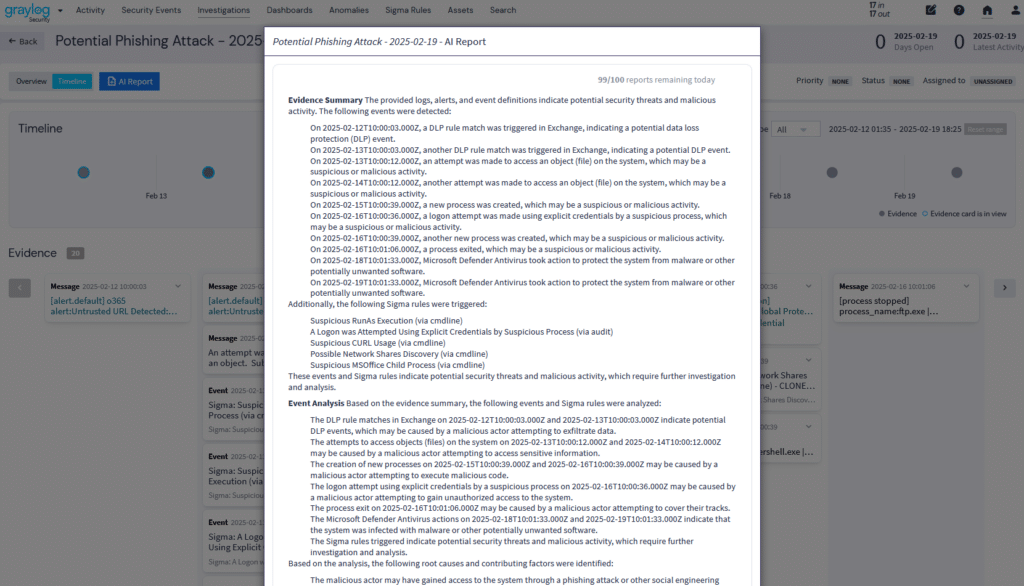
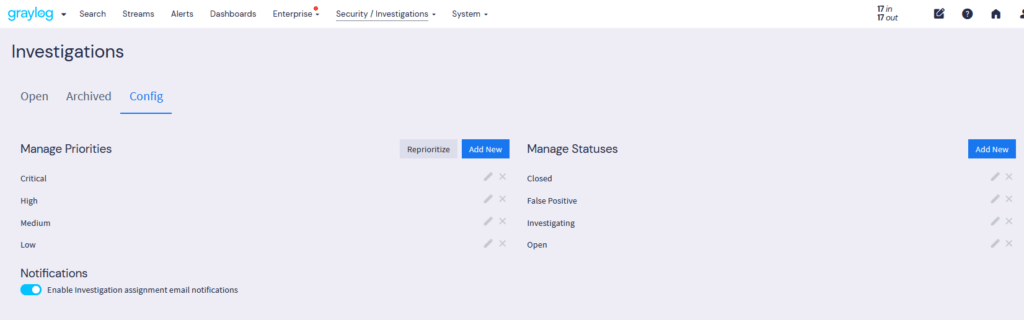
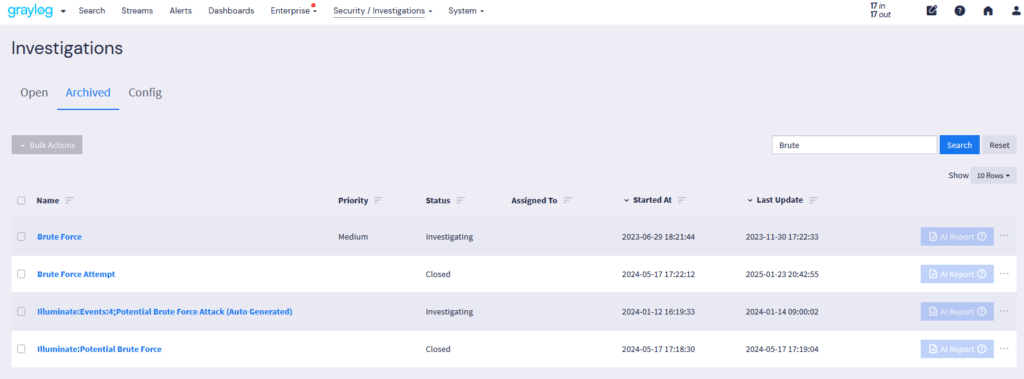
Managing investigations—searching for answers, collecting evidence, collaborating with team members, and recommending remediation—is critical for cybersecurity professionals. Graylog Investigations simplifies this process with centralized incident tracking, AI-driven analysis, and seamless collaboration.