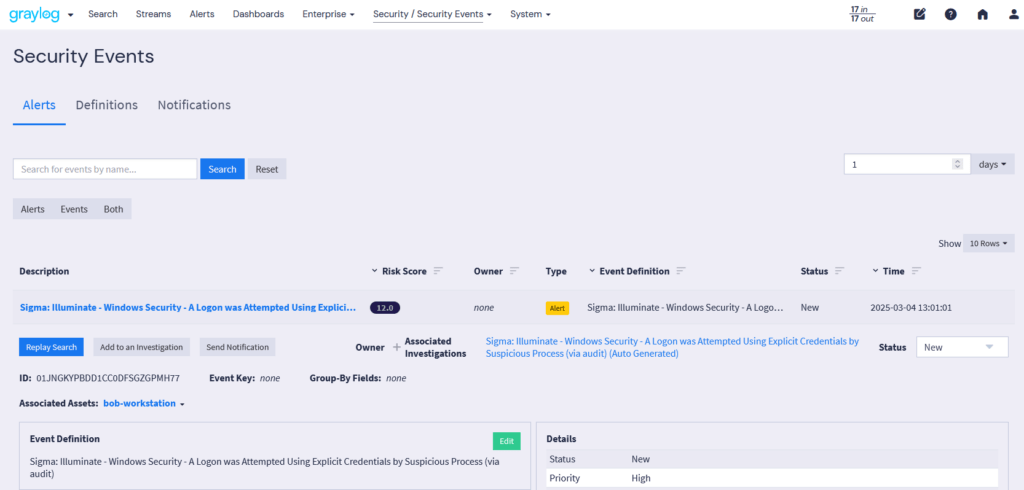
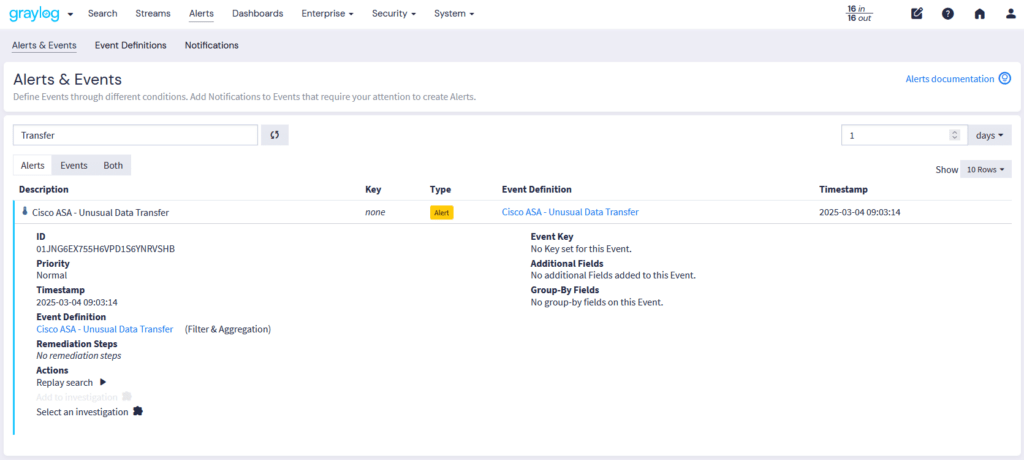
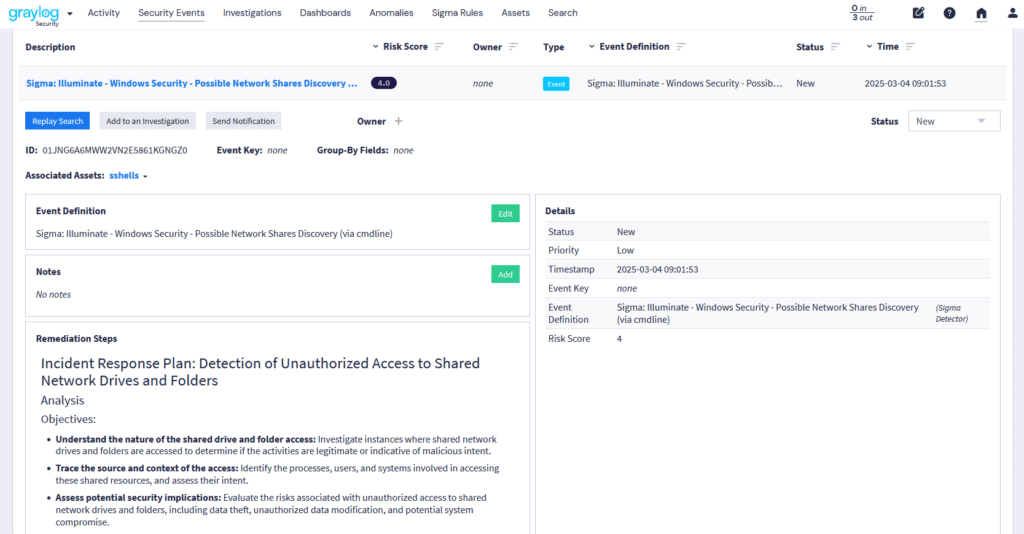
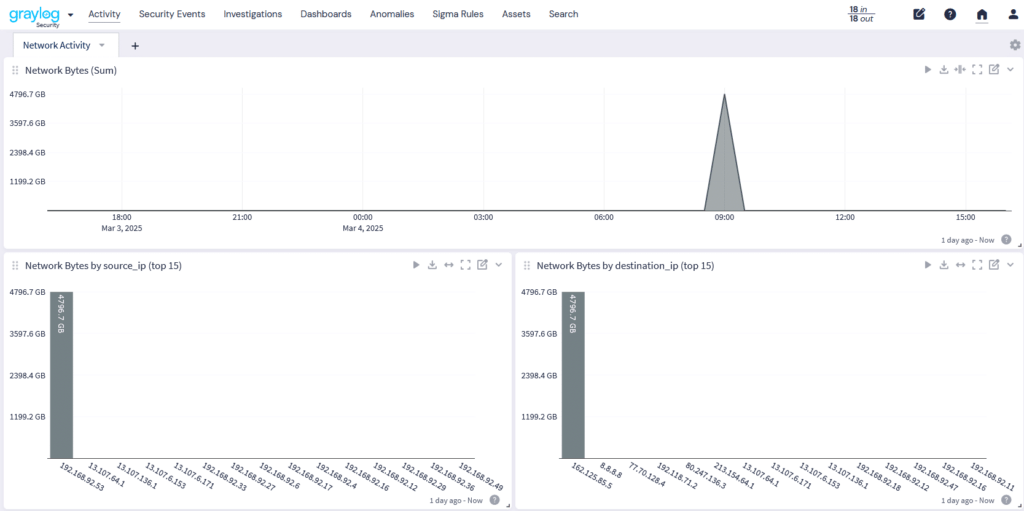
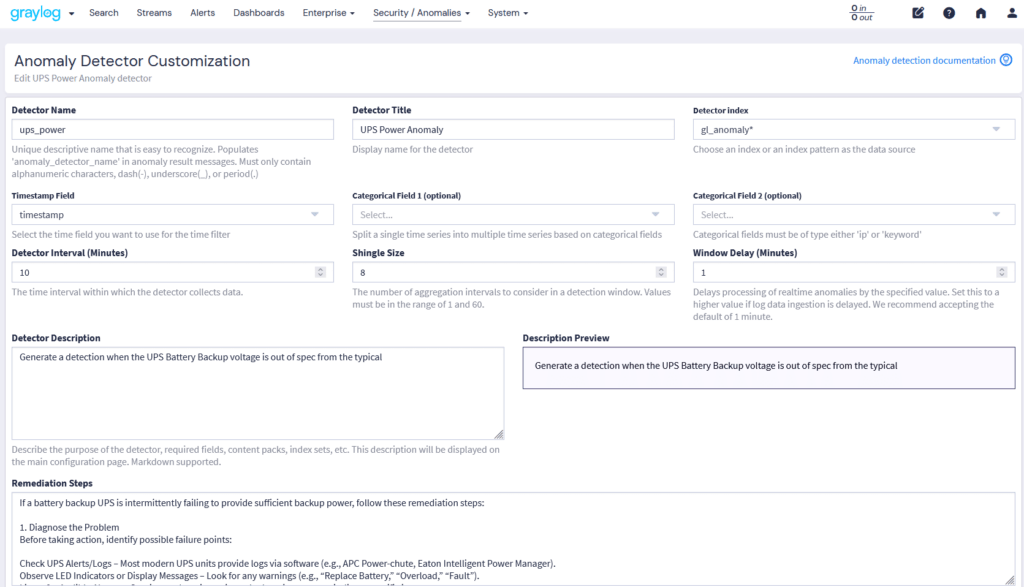
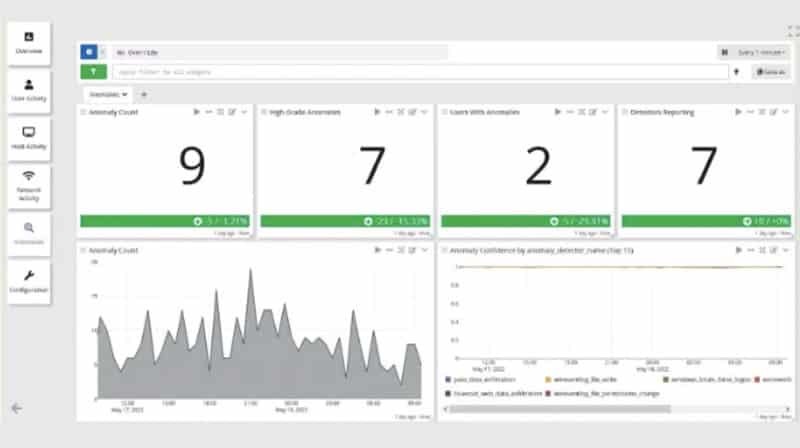
Abnormal access attempts threaten Windows, Linux, applications, cloud platforms, and firewalls. Failed logins on Windows can trigger lockouts, while brute-force attacks on Linux target SSH credentials, requiring firewall intervention. In the cloud, repeated failures may suspend accounts, with firewalls blocking suspicious IPs. Strong authentication, real-time monitoring, and proactive security are essential to prevent breaches.