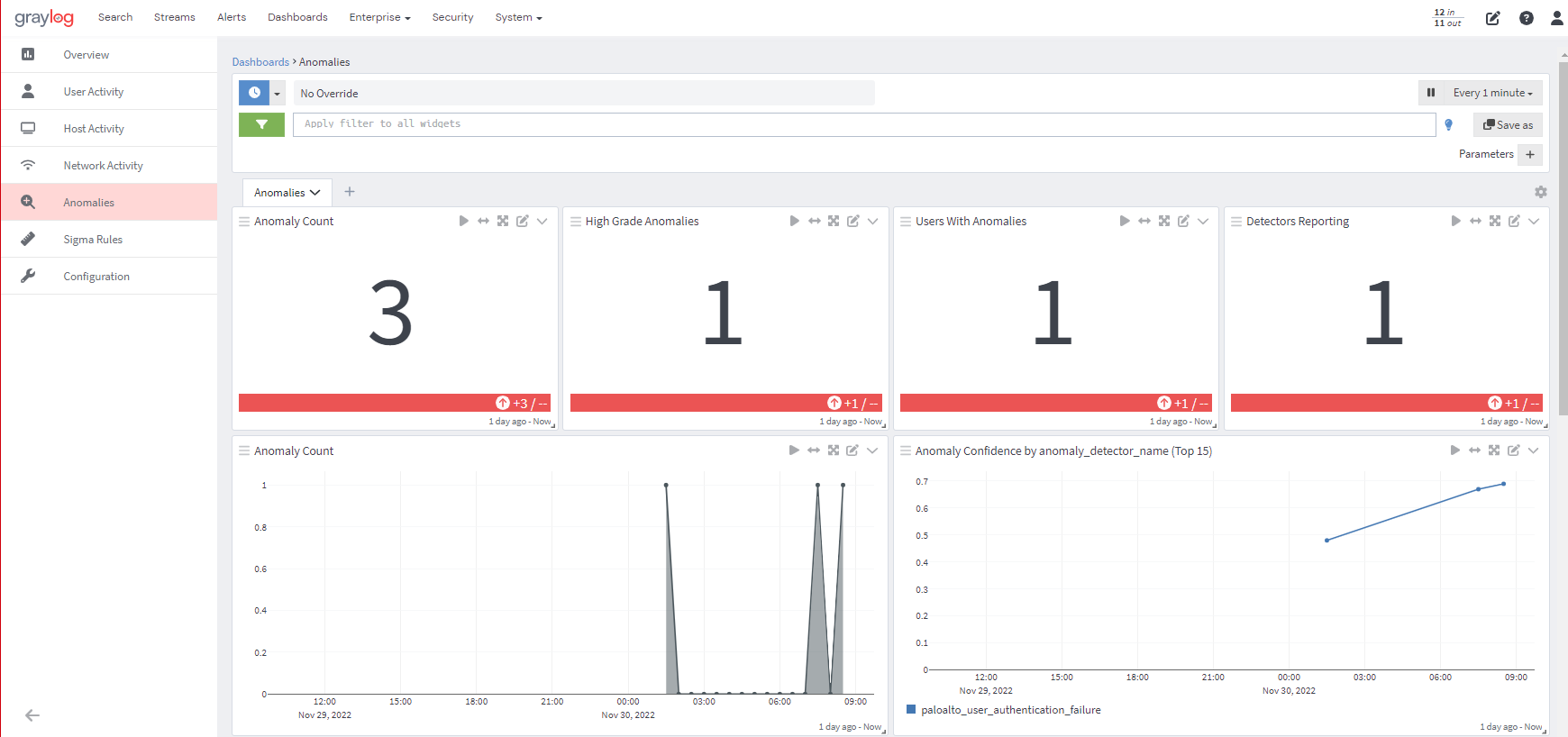
Anomaly Detection, one of the powerful features in Graylog Security, provides you with UEBA capabilities at scale, running Artificial Intelligence / Machine Learning (AI/ML) that identifies deviations from “normal” behavior for users and entities (UEBA), creating high-fidelity alerts.

Custom Anomaly Detectors
Graylog Security provides numerous out-of-the-box anomaly detectors through the Illuminate content pack that can be run simultaneously so security analysts can easily analyze data from different sources for unusual behavior. In addition to the out-of-the-box anomaly detectors, security analysts can now add additional detection capabilities by customizing anomaly detectors in OpenSearch that can be shared with the Graylog Community.

Real Learning With Dynamic AI
Spend less time reacting and more time securing with Graylog’s AI/ML Anomaly Detection that can:
- Self-learn with a minimum amount of historical data
- Improve over time without manual tuning
- Adapt to new data sets, organizational priorities, custom use cases, and more
- Incorporate out-of-the-box scenarios mapped Community standards, and real-life adversarial examples
- Search for and identify unusual activity by users and entities
Defining Baselines
Know your “normal.” Defining normal user behavior to prevent insider threats is increasingly challenging, with people wearing different hats while accessing and sharing more data.
Anomaly Detection AI/ML uses your data to define baselines by combining:
- User and Entity profiling based on real-life insider threat use cases
- Network profiling learns networks and automatically adapts to environments
Risk-Modeling For Insider Threat Detection
Use built-in knowledge from real-life examples mapped to the MITRE ATT&CK framework, including:
- Corporate espionage
- Sabotage
- Data exfiltration
- Fraud
Visibility Into Credential-Based Attacks
Gain visibility into the risky activities that indicate credential-based attacks. Graylog Anomaly Detection provides high-fidelity alerts that detect attacks that “hardcoded” correlation alerts might miss.

Graylog’s Anomaly Detection can detect credential-based attacks, like brute force, and lateral movement within your environment by aggregating, normalizing, and correlating events like:
- Unauthorized web activity
- New host authentication
- Authentication using new application
- Account creation
- Account deletion
- Short-lived account creation
- Local privilege escalation
- Global privilege escalation
- Singe host malware infection spikes
- Multiple host malware outbreaks
- Audit log deletion
Cloud-Access Monitoring
Not every data change or download is necessary. Sometimes, it’s accidental, and other times malicious.
Graylog’s Anomaly Detection gives you the visibility you need by detecting risky activity spikes like:
- File permission changes
- File modifications
- File deletions
Prevent malicious or inappropriate data exfiltration by reviewing download activity across:
- Rare websites
- Webmail
- Email servers
- Removable media
- Rare processes
- DNS
Scalability and Speed
Get alerts that make investigations meaningful by reducing the noise from cloud applications and engaging in lightning-fast investigations.
Graylog Anomaly Detection aggregates and correlates insights from across your environment, bringing together UEBA, event log, and threat intelligence data for high-fidelity alerts with the ability to:
- Ingest any log source from anywhere
- Easily parse, enrich, and normalize data
- Seamlessly integrate with common security tools
- Intuitively investigate threats paired with Graylog’s lightning-fast search engine to get to the root cause and eliminate cybersecurity risks in hours, not weeks or months
- Search terabytes in milliseconds
- Easily provide meaningful context
- Leverage integrated dashboards and alerts


