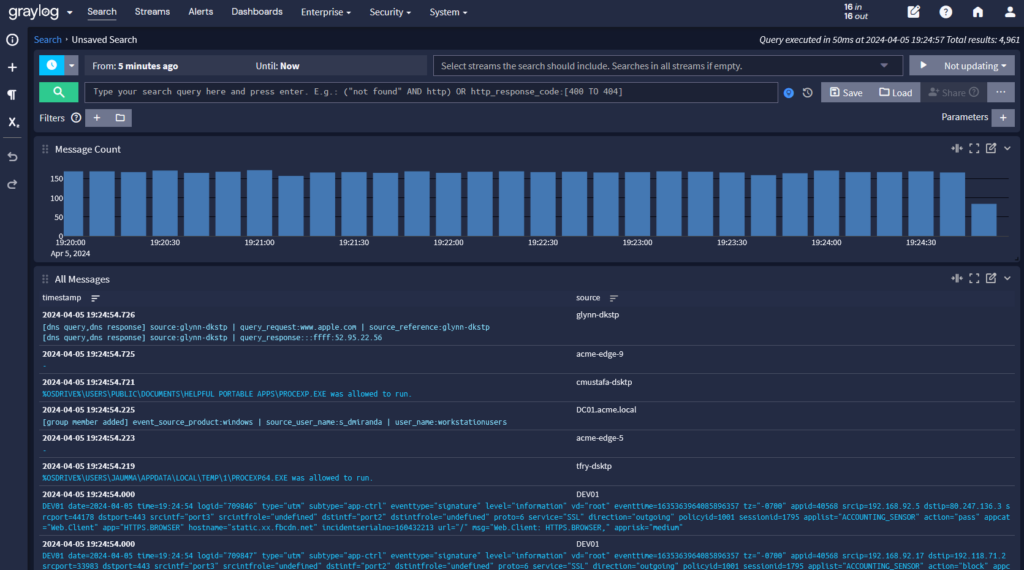
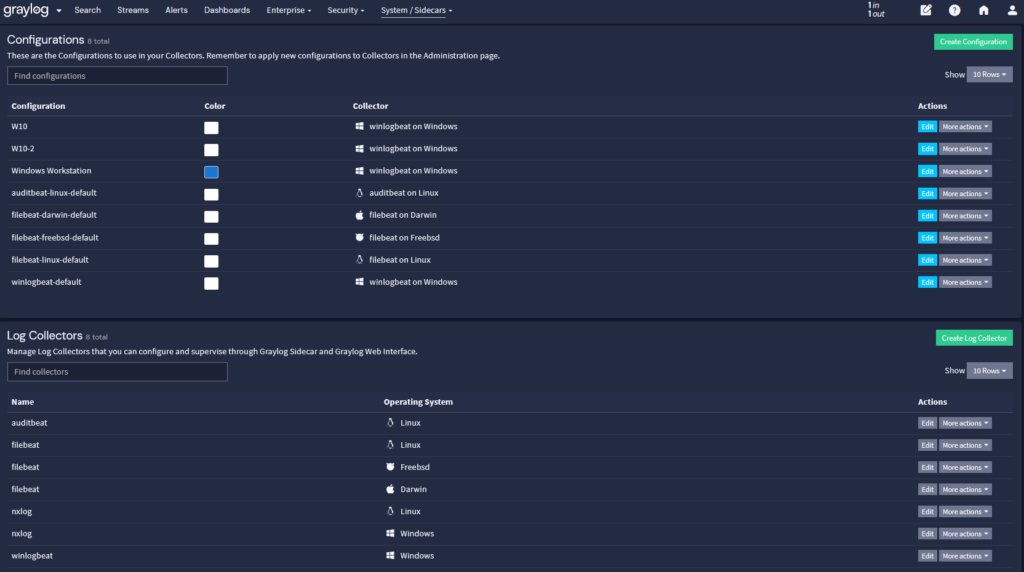
Each log shipper is configured to collect specific logs from their respective sources. For example:
NXLog: For its versatility in collecting logs from various sources and its ability to transform and relay logs in different formats from multiple operating systems.
Winlogbeat: Specialized in forwarding Windows event logs with minimal impact on system performance, keeping your Windows infrastructure transparent and secure.
Filebeat: Ideal for monitoring log files, collecting log events, and forwarding them to our platform for analysis. Its lightweight nature ensures efficiency and reliability for shipping logs from multiple operating systems and devices.
Metricbeat: An application used to ship metrics from operating systems from the services running on those servers.