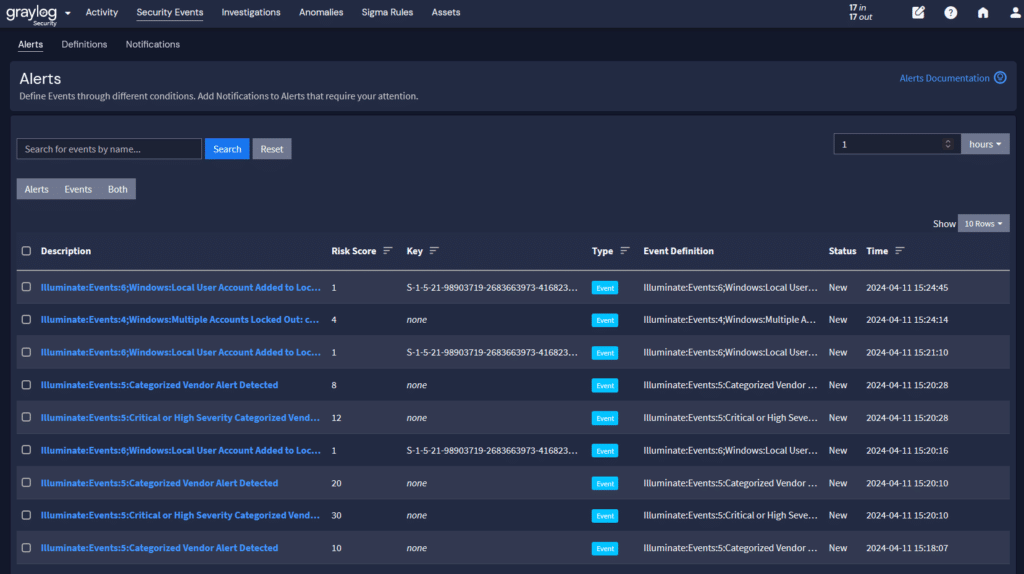
Alerting is activated by event definitions, with a correlation engine that connects events intelligently, providing context and significance through anomaly detection. This system is elevated within Graylog by Sigma Rules—globally recognized, open-source alerting rules integrated with the MITRE ATT&CK framework. Graylog further eases the burden of a security analyst by providing a curated set of alerts from SOC Prime, removing the need for users to develop their own rules.