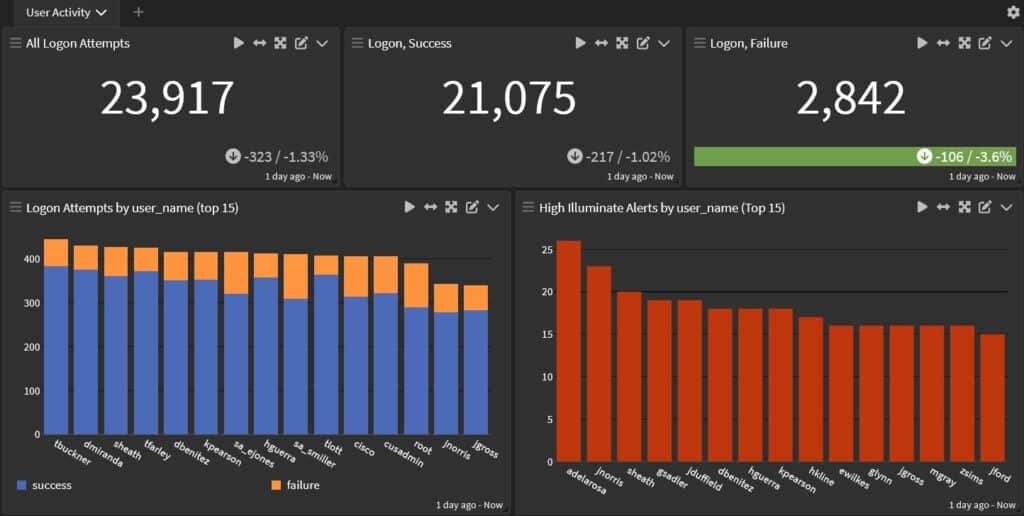
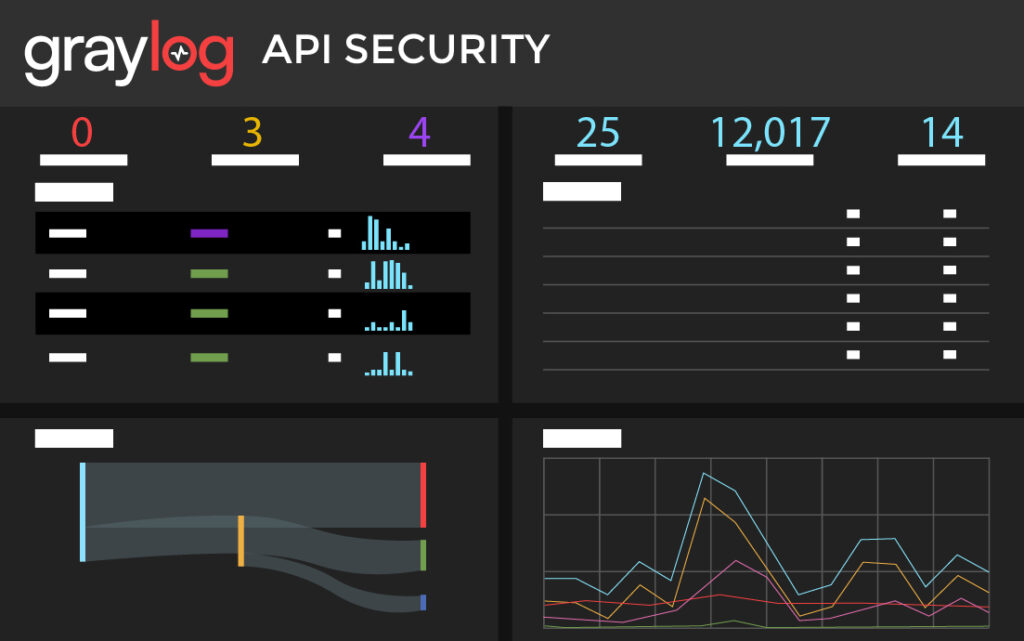
In today’s hyper-connected digital landscape, organizations face the daunting challenge of ensuring their operations comply with an ever-evolving regulatory standard. With the stakes higher than ever and regulatory bodies becoming more stringent, businesses are constantly on the lookout for efficient and robust solutions to maintain compliance and safeguard their reputation.