For Star Trek fans, space may be the final frontier, but in security, discovering Application Programming Interfaces (APIs) could be the technology equivalent. In the iconic episode “The Trouble with Tribbles,” the legendary starship Enterprise discovers a space station that becomes overwhelmed by little fluffy, purring, rapidly reproducing creatures called “tribbles.” In a modern IT department, APIs can be viewed as the digital tribble overwhelming security teams.
As organizations build out their application ecosystems, the number of APIs integrated into their IT environments continues to expand. Organizations and security teams can become overwhelmed by the sheer number of these software “tribbles,” as undiscovered and unmanaged APIs create security blindspots.
API discovery is a critical component for any security program because it expands the organization’s attack surface.
What is API discovery?
API discovery is a manual or automated process that identifies, documents, and catalogs an organization’s APIs so that security teams can monitor the application-to-application data transfers. To manage all APIs that the organization integrated into its ecosystem, organizations need a comprehensive inventory that includes:
- Internal APIs: interfaces between a company’s backend information and application functionality
- External APIs: interfaces exposed over the internet to non-organizational stakeholders, like external developers, third-party vendors, and customers
API discovery enables organizations to identify and manage the following:
- Shadow (“Rogue”) APIs: unchecked or unsupervised APIs
- Deprecated (“Zombie”) APIs: unused yet operational APIs without the necessary security updates
What risks do undocumented and unmanaged APIs pose?
Threat actors can exploit vulnerabilities in these shadow and deprecated APIs, especially when the development and security teams have no way to monitor and secure them.
Unmanaged APIs can expose sensitive data, including information about:
- Software interface: the two endpoints sharing data
- Technical specifications: the way the endpoints share data
- Function calls: verbs (GET, DELETE) and nouns (Data, Access) that indicate business logic
Why is API discovery important?
Discovering all your organization’s APIs enhances security by incorporating them into:
- Risk assessments: enabling API vulnerability identification, prioritization, and remediation
- Compliance: mitigate risks arising from accidental sensitive data exposures that lead to compliance violations, fines, and penalties
- Vendor risk management: visibility into third-party security practices by understanding the services, applications, and environments that they can impact
- Incident response: faster detection, investigation, and response times by understanding potential entry points, impacted services, and data leak paths
- Policy enforcement: ensuring all internal and external APIs follow the company’s security policies and best practices
- Training and awareness: providing appropriate educational resources for developers and IT staff
Beyond the security use case, API discovery provides these additional benefits:
- Faster integrations by understanding available endpoints, methods, and data formats
- Microservice architecture management by tracking services, health status, and interdependencies
- Enhanced product innovation and value by understanding API capabilities and limitations
- Increased revenue by understanding API usage
Using automation for API discovery
While developers can manually discover APIs, the process is expensive, inefficient, and risky. Manual API discovery processes are limited because they are:
- Time-consuming: With the average organization integrating over 9,000 known APIs, manual processes for identifying unknown or unmanaged APIs can be overwhelming, even in a smaller environment.
- Error-prone: Discovering all APIs, including undocumented ones and those embedded in code, can lead to incomplete discovery, outdated information, or incorrect documentation.
- Resource-intensive: Manual discovery processes require manual inventory maintenance.
Automated tools make API discovery more comprehensive while reducing overall costs. Automated API discovery tools provide the following benefits:
- Efficiency: Scanners can quickly identify APIs, enabling developers to focus on more important work.
- Accurate, comprehensive inventory: API discovery tools can identify embedded and undocumented APIs, enhancing security and documentation.
- Cost savings: Automation takes less time to scan for updated information, reducing maintenance costs.
What to look for in an API discovery tool
While different automated tools can help you discover the APIs across your environment, you should know the capabilities that you need and what to look for.
Continuous API Discovery
Developers can deliver new builds multiple times a day, continuously changing the API landscape and risk profile. For an accurate inventory and comprehensive visibility, you should look for a solution that scans:
- All API traffic at runtime
- Categorizes API calls
- Sorts incoming traffic into domain buckets
For example, when discovering APIs by domain, the solution includes cases where:
- Domains are missing
- Public or Private IP addresses are used
With the ability to identify shadow and deprecated APIs, the solution should give you a way to add domains to the:
- Monitoring list so you can start tracking them in the system
- Prohibited list so that the domain should never be used
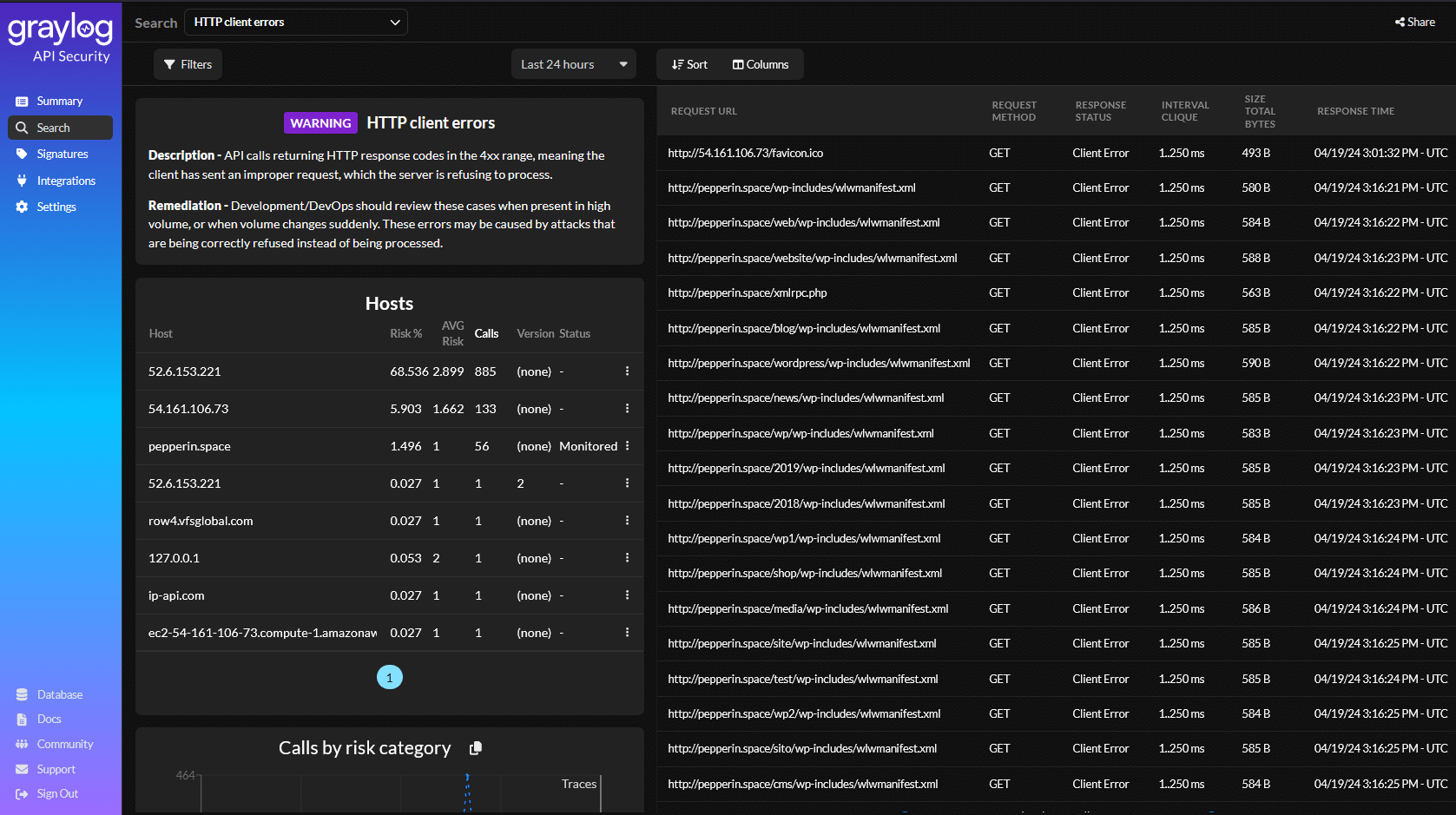
Vulnerability Identification
An API discovery solution that analyzes all traffic can also identify potential security vulnerabilities. When choosing a solution, you should consider whether it contains the following capabilities:
- Captures unfiltered API request and response detail
- Enhances details with runtime analysis
- Creates an accessible datastore for attack detection
- Identified common threats and API failures aligned to OWASP and MITRE guidance
- Automatic remediation tops with actionable solutions that enable the teams to optimize critical metrics like Mean Time to Response (MTTR)
Risk Assessment and Scoring
Every identified API and vulnerability increases the organization’s risk. To appropriately mitigate risk arising from previously unidentified and unmanaged APIs, the solution should provide automated risk assessment and scoring. With visibility into the type of API and the high-risk areas that should be prioritized, Security and DevOps teams can focus on the most risky APIs first.
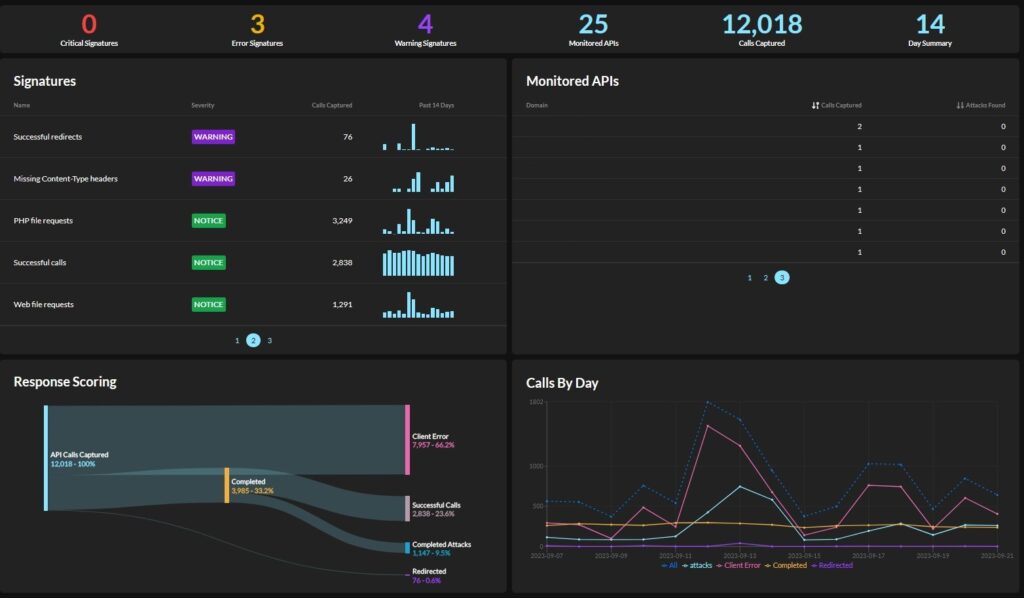
Graylog API Security: Continuous, Real-Time API Discovery
Graylog API Security is continuous API security, scanning all API traffic at runtime for active
attacks and threats. Mapped to security and quality rules, Graylog API Security captures
complete request and response details, creating a readily accessible datastore for attack
detection, fast triage, and threat intelligence. With visibility inside the perimeter,
organizations can detect attack traffic from valid users before it reaches their applications.
Graylog API Security captures details to immediately identify valid traffic from malicious
actions, adding active API intelligence to your security stack. Think of it as a “security
analyst in-a-box,” automating API security by detecting and alerting on zero-day attacks
and threats. Our pre-configured signatures identify common threats and API failures and
integrate with communication tools like Slack, Teams, Gchat, JIRA or via webhooks.